What are Some Best Practices for Researchers to Protect Research Data?
- Remain Current with Cybersecurity Practices
- Review information at the TTU Cybersecurity website
- Be alert to announcements that pertain to cybersecurity practices.
- Review security logs daily (System Administrators).
- Stay current by reading technological articles.
- Install Anti-virus Software
- Symantec Endpoint Protection is available for download, free of charge, through the eRaider website. In addition to Symantec, other anti-virus applications may be considered.
- Install a Firewall
- Update and Patch Operating System
- Windows OS
- Enable automatic critical updates for Windows on a weekly basis. Instructions are available at IT Help Central.
- Use Microsoft Windows Update to manually install other updates on a weekly basis
- Unix / Linux OS
- Most UNIX or Linux operating system vendors release security patches regularly. You should check the vendor websites for new patches at least weekly, and immediately after any announcement of a new vulnerability.
- Most vendors also allow users to subscribe to security mailing lists for their operating systems.
- Windows OS
- Data Classification
- Research data is classified to identify access control, data encryption and backup
requirements. The following matrix may be used as a guide to classify your information
and data:
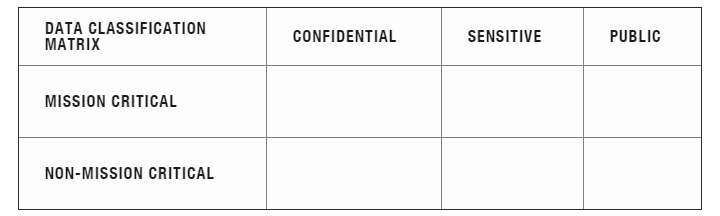
- Research data is classified to identify access control, data encryption and backup
requirements. The following matrix may be used as a guide to classify your information
and data:
-
- Ensure that access to all confidential and sensitive data is managed appropriately.
- Use strong passwords. (Password integrity relies heavily upon the password length, complexity, reuse, and aging.)
- Change the default administrator accounts and passwords.
- Social Security numbers must not be used as a primary or secondary identifiers. Use university provided eRaider authentication for access computer systems and applications.
- For database and web applications, use eRaider authentication. Programming assistance for the front-end authentication is provided by Technology Support.
- You may choose to enhance the security of data on the hard drive by the following
two methods:
- Restrict user access to the directory file structure.
- Restrict user permissions to the directory file structure.
- Lock workstations or use password protected screen savers when users are away.
- For secure remote access to university computer systems from off-campus, use Virtual Private Networking (VPN). Information is available at IT Help Central.
- Other practices and tools may be used to increase the security of the system. For example, you may take periodic system snapshots by using a security scanner available from Microsoft.
- Ensure that access to all confidential and sensitive data is managed appropriately.
- Data Backup Options
- The University offers a central data backup service for computers within the TTU domain with mission critical data.
- You may also choose to perform your own data backup.
- Data Encryption
- Data encryption may be used to further protect confidential and sensitive research data.
- If data is encrypted, ensure that the encryption will stay with the data as it travels through the network, web servers, application servers, and database server.
- To encrypt confidential and sensitive email communications, view information available from VeriSign.
- Protection of Research Labs
- Secure physical access to research labs
- Contact the University Police Department for consultation on ways to protect access to research labs.
- A criminal background check on employees is strongly recommended.
- Consult with TTU Environmental Health and Safety to guard against environmental hazards
- Secure physical access to research labs
For more information or to pursue options outlined above, please contact the HPCC at 806-742-4350.
Related Information
Related Resources
- Academic Calendars
- Blackboard@TTU
- Campus Bookstore
- Departments
- Human Resources
- IT Division
- Laws & Policies for Computer Use
- Office of the President
- Office of the Provost
- Official Publications
- Operating Policies & Procedures
- Podcasting Roundtable
- Protecting Research Data
- Raiderlink
- Student Disability Services
- Technology Support
- Teaching, Learning, & Professional Development Center
- Transportation & Parking Services
IT Services for Researchers
-
Address
Texas Tech University, 2500 Broadway, Lubbock, TX 79409 -
Phone
806.742.2011 -
Email
webmaster@ttu.edu
